Whoa! The first time I clicked “Connect” on a Solana dApp, my heart skipped. Seriously? It felt both magical and terrifying. My instinct said: back away slowly. But curiosity won. At first I thought a browser extension would be clunky and insecure, but then a few honest tests changed my mind—slowly, and with a few stumbles along the way.
Here’s the thing. Browser wallets for Solana give near-instant transactions with tiny fees, and that changes how you interact with the whole web3 experience. Short waits, low cost. That combo matters. On one hand it feels like an upgrade from old-school wallets; on the other, there are real UX and security trade-offs that bug me.
I’ll be candid: I’m biased toward wallets that keep private keys client-side and minimize permissions. I’m also stubborn about avoiding sketchy sites. That bias colors how I evaluate extensions and apps. Initially I favored convenience; later, repeated usage taught me to favor deliberate control—especially when apps ask for signatures that could be broad or vague.
Fast reactions matter. Hmm… when a dApp requests a wallet connect, my gut flags anything that tries to request excessive permissions. Something felt off about blanket approvals. Actually, wait—let me rephrase that: blanket approvals are fine in theory, but in practice they often lead to future headaches when malicious contracts piggyback on earlier permissions.
So here’s a practical thread: how to think about a Solana browser extension versus the Phantom app experience, and how to make a smart, low-friction choice without giving up security. I’ll share what I do, what I’ve seen, and somethin’ I learned the hard way—so you don’t have to.
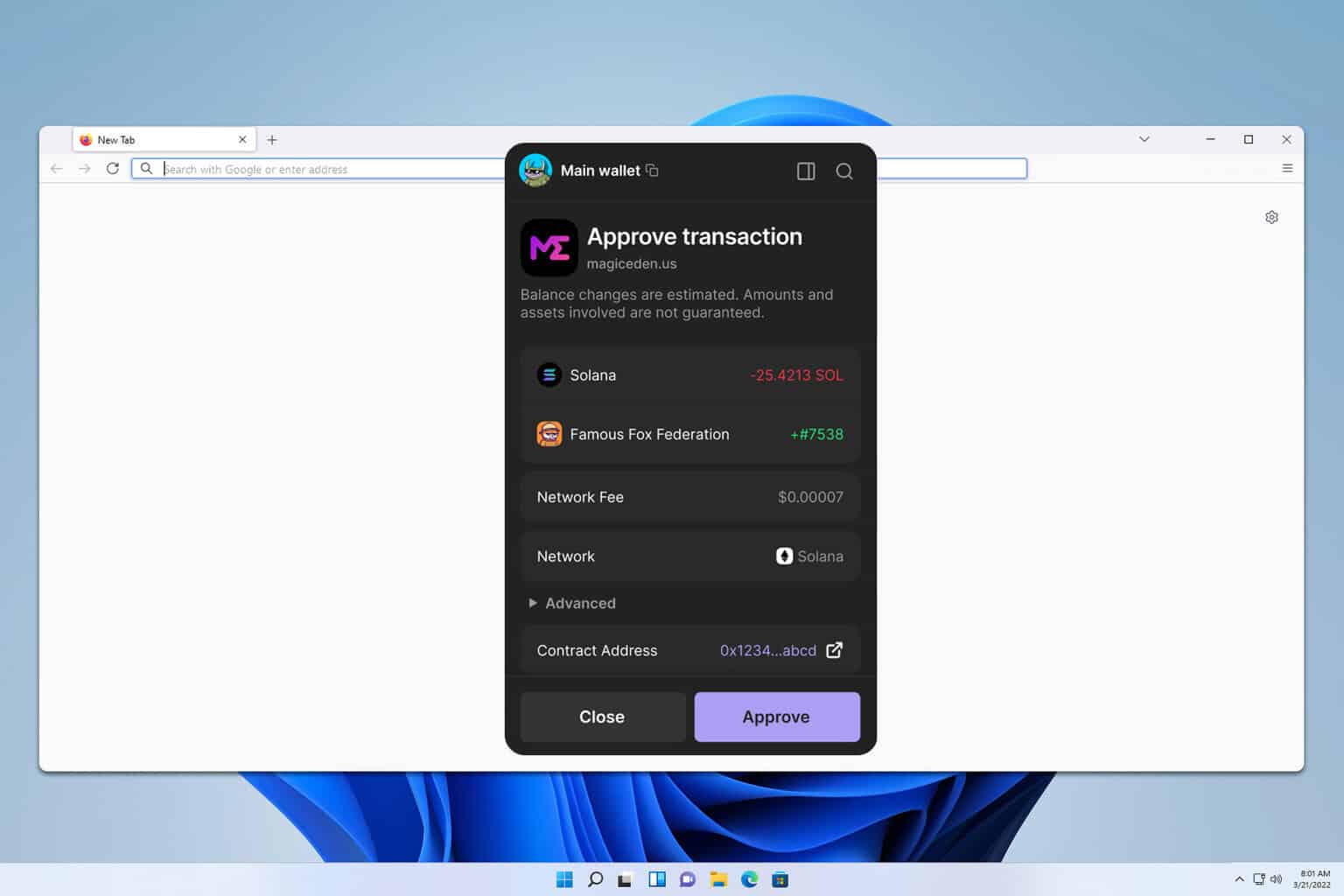
A real-world checklist for picking a Solana browser wallet
Okay, so check this out—before installing any extension, I run a quick mental checklist. Who built it? Is it audited? How many installs or users? Does it ask for seed words anywhere? How granular are the permissions? These are basic, but very very important. I rate each item quickly and then dig in where something looks off.
Security first. Keep keys client-side. Short sentence. Prefer extensions that offer hardware wallet support and transaction previews. Longer thought that matters: when an extension presents an opaque signature request or a non-descriptive transaction summary, I pause and look for the raw transaction data or a decoded preview, because that’s where you can catch replay attacks or unintended approvals before they happen.
Usability next. You want fast confirmations and clear UX for networks and tokens. Medium sentence here to keep it readable and useful. Too many options in the UI can make mistakes more likely. On the flip side, overly simplified wallets hide nuance, and that can cause trouble for power users.
Compatibility matters. Most Solana dApps expect a browser wallet that supports the standard provider APIs. If the extension is forked or missing features, you’ll hit errors. I’ve seen weird failures where a dApp tries to fetch the wallet provider and the extension doesn’t expose the right API—annoying, and avoidable with careful choice.
One more practical rule: use a seeded wallet for everyday small amounts and a hardware-backed wallet for large sums. It feels obvious, but people skip it. I’m not 100% sure about transfer thresholds, but for me that split reduces stress and makes experimental dApp use safer.
Why Phantom’s extension and app stand out (and the one link I’ll recommend)
Short burst: Really? Yes. Phantom nails the balance between ease and safety for most users. The UI is clear, transaction previews are readable, and the team iterates quickly. On the other hand, no product is perfect, and Phantom’s frequent updates mean you should glance at permissions after big changes—don’t just auto-update blindly.
If you want a quick way to try it, go to the official place to get the extension: phantom wallet download extension. I’m linking that as the go-to entry, since finding the authentic extension matters—phishing clones are real and they look identical at first glance. Check the URL. Check the publisher. If somethin’ smells off, don’t proceed.
When installing, watch for requests to export or reveal your seed phrase. Never, ever paste your seed into a site. Short sentence. Keep it offline. Phantom supports hardware wallets and that integration is a huge plus for people holding real value long-term. Longer caution: even with hardware support, some signing workflows can be complex, so learn the process on low-value transactions before you commit big funds.
My instinct says: use the extension for everyday stuff and the mobile app for on-the-go viewing and quick approvals. Though actually, wait—let me correct that bias: mobile apps can be just as secure as desktop extensions if you maintain device hygiene and use OS-level protections like biometrics. On the other hand, phones are lost more often, so backups are essential.
Common pitfalls I’ve seen (and how to avoid them)
Short. Phishing is the biggest risk. Medium sentences to explain it: attackers create fake dApps and extension clones to capture seed phrases or trick users into signing malicious transactions. Longer thought: once a signature is granted for a transaction that allows token transfer authority, rogue actors can move funds, and often users don’t realize until it’s too late because they approved a seemingly legitimate action earlier.
Permission creep is subtle. You grant an approval for a specific contract and later find it can be reused. Watch for “approve all” style prompts. I learned this after a small but painful loss—lesson stuck. It’s human to rush; these interfaces exploit that haste.
Extensions with suspicious permission requests or vague transaction summaries are red flags. Short. If a signing request shows a hex blob with no decoded content, pause. Medium explanation: request the decoded transaction via the extension or use a public decoder to inspect what you’re signing. Hard truth: many users skip this because it feels technical, but that small pause is powerful insurance.
Double-check network settings. Sometimes an extension switches networks or adds RPC endpoints that you didn’t configure, and that can route you through malicious nodes. Keep your RPC endpoints known and, when possible, use reputable endpoints with rate limits and monitoring.
Also—this bugs me—people re-use the same seed phrase across extensions or apps. Don’t do that. Use separate accounts, or at least separate derivation paths for experimentation. I’m not being dramatic; it’s a simple hygiene practice that saves headaches.
FAQ
Is a browser extension safe for holding large amounts of SOL?
Short answer: no. Use hardware wallets for large holdings. Medium: browser extensions are great for convenience and small, frequent interactions, but they’re exposed to the browser environment, which can be compromised by malicious extensions or compromised sites. Longer caveat: if you pair your extension with a hardware wallet, or use the app only with segregated accounts and small balances, the risk profile becomes much more manageable.
Should I trust a newly released extension version immediately?
Don’t rush it. Wait to see community feedback or look for an official changelog and audit notes. If a release changes permissions or request flow, be especially skeptical. Again, I’m biased toward conservative updates, but that saves money.
Final thought—no punchline, just practice. Start small. Test transactions. Keep seed phrases offline. Use hardware where it counts. My approach evolved from naive eagerness to cautious practice, and that evolution matters because real money was at stake. Initially I rushed; later I slowed down, and that saved me. I’m sharing these textures because you probably want to move fast and not get burned—same as me.
So go ahead, try the extension if you want to build familiarity, but treat every signature like a permission slip and every new site like a stranger at the door. Hmm… trust cautiously, play boldly, and back up your keys.

